An Artificial Neural Network-Based Caller Authentication and Identification Algorithm in Cellular Communication Networks
DOI:
https://doi.org/10.58190/ijamec.2024.111Keywords:
Artificial Neural Networks, Caller Authentication, Cellular Communication, Prevention of Black Market SIMs, SIM User IdentificationAbstract
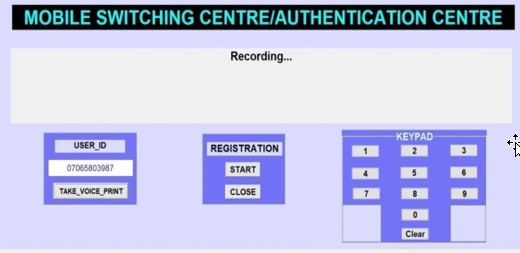
Cellular communication companies have created tens of thousands of jobs within the industry. However, while business opportunities have expanded for legitimate enterprises, criminal gangs have also exploited the new business environment to further their illegal activities. Weaknesses in the authentication algorithm allow criminals to commit fraud while remaining anonymous, thereby facilitating wireless crime. This paper presents the development of an artificial neural network-based caller authentication and identification algorithm for cellular communication networks that addresses these weaknesses. Voice data were collected from volunteer participants and the Mozilla Common Voice (MCV) database. Voice feature vectors were extracted from the voice data using the Mel Frequency Cepstral Coefficient (MFCC) technique. The extracted voice feature vectors were used to train a Multilayer Perceptron (MLP) neural network for voiceprint generation. The MLP neural network architecture was optimized through Neural Architecture Search (NAS) using the Neural Network Intelligence (NNI) toolkit. The optimized MLP neural network architecture was trained with the extracted voice feature vectors to generate a voiceprint generation model. The developed voiceprint model was then deployed to create an artificial neural network-based caller authentication and identification algorithm in cellular communication networks. The developed algorithm was evaluated in the cellular communication emulation setup using accuracy, false acceptance rate (FAR), and false rejection rate (FRR) as metrics. The results of the performance evaluation of the developed algorithm for authenticating first-time users of a new SIM and identifying third-party SIM users both showed 100% accuracy, 0% FAR, and 0% FRR. These results indicate that the developed algorithm has strong potential to prevent the use of black market SIMs and deter perpetrators from using third-party SIMs to access network services while remaining anonymous.
Downloads
References
[1] Alezabi, K., A., Hashim, F., Hashim, S.J., & Ali, B.M. (2014). An Efficient Authentication and Key Agreement Protocol for 4G (LTE) Networks. 2014 IEEE Region 10 Symposium. Pp. 502 – 507. https://doi.org/10.1109/TENCONSpring.2014.6863085
[2] Asda Mobile. (2022). How to unlock your phone with a PUK code. https://mobile.asda.com/scoop/how-to-unlock-your-phone-with-a-puk-code
[3] Botalb, A., Moinuddin, M., Al-Saggaf, U. M., & Ali, S. S. A. (2018). Contrasting Convolutional Neural Network (CNN) with Multi-Layer Perceptron (MLP) for Big Data Analysis. 2018 International Conference on Intelligent and Advanced System (ICIAS). doi:10.1109/icias.2018.8540626
[4] Chintalapati, P.V., Babu, G.R., Sree, P.K., Kode, S.K., Kumar, G.S. (2023). Usage of AI Techniques for Cyberthreat Security System in Android Mobile Devices. In: Hassanien, A.E., Castillo, O., Anand, S., Jaiswal, A. (eds) International Conference on Innovative Computing and Communications. ICICC 2023. Lecture Notes in Networks and Systems, vol 703. Springer, Singapore. https://doi.org/10.1007/978-981-99-3315-0_33
[5] Douglas, K., & Mumbi, C. (2018). A Survey of Android Mobile Phone Authentication Schemes. Mobile Networks and Applications. doi:10.1007/s11036-018-1099-7
[6] Fan, C. I., Shih, Y. T., Huang, J. J. & Chiu, W. R. (2021). Cross-Network-Slice Authentication Scheme for the 5th Generation Mobile Communication System. IEEE Transactions on Network and Service Management, 18(1). Pp. 701-712. doi:10.1109/TNSM.2021.3052208.
[7] GSMA. (2016). Mandatory registration of prepaid SIM cards: Addressing challenges throughbestpractice. https://www.gsma.com/publicpolicy/wpcontent/uploads/2016/04/GSMA2016_Report_MandatoryRegistrationOfPrepaidSIMCards.pdf
[8] Ibrahim, A. J., &Jauro, U. A. (2021). Bio-metric encryption of data using voice recognition. Autom. Control Intell. Syst, 9 (3).
[9] Ibrahim, Q., Abdulghani, N. (2012). Security enhancement of voice over Internet protocol using speaker recognition technique. IET Communications. 6 (6), pp. 604 – 612.
[10] Indriyani, & Aprinia, D. (2022). Role of Truecaller application in preventing phone call and text message scams. Jurnal Mantik, 6(2), 1475-1483. https://doi.org/10.35335/mantik.v6i2.2533
[11] Jung, E., & Hong, K. (2015). Biometric verification based on facial profile images for mobile security. Journal of Systems and Information Technology, 17(1), 91– 100. doi:10.1108/jsit-03-2014-0020
[12] Kazmi, S. H. A., Hassan, R., Qamar, F., Nisar, K. & Ibrahim, A. A. A. (2023). Security Concepts in Emerging 6G Communication: Threats, Countermeasures, Authentication Techniques and Research Directions. MDPI, 15(6). https://doi.org/10.3390/sym15061147
[13] Khan, A. S., Javed, Y., Saqib, R. M., Ahmad, Z., Abdullah, J., Zen, K., Abbasi, I. A., Khan, N. A. (2022). Lightweight Multifactor Authentication Scheme for NextGen Cellular Networks. IEEE Access, vol. 10. doi: 10.1109/ACCESS.2022.3159686
[14] Luo, Q. & Zhang, Z. (2023). The Secure Data Transmission Method of a Cellular Communication Network Based on the Asymmetric Encryption Algorithm. Journal of Communications, 18(2). Pp 82 – 88. doi:10.12720/jcm.18.2.82-88
[15] Miesle, P. (2023, September). What is cosine similarity: A comprehensive guide. Datastax. https://www.datastax.com/guides/what-is-cosine-similarity
[16] Mohammed, A. (2023). How to enable SIM lock on your Android phone: Prevent malicious SIM card use by adding an extra layer of security. Android Police. https://www.androidpolice.com/enable- sim-lock-android-phone-protection/
[17] Nakarmi, P. K. (2021). Cheatsheets for authentication and key agreement in 2G, 3G, 4G, and 5G. Ericsson. https://arxiv.org/pdf/2107.07416v1.pdf
[18] Okonji, E. (2022, March 04). Terrorism: No Unregistered SIM Cards on Operators’ Network. Telcos Insist. Thisday. https://www.thisdaylive.com/index.php/2022/04/03/terrorism-no- unregistered-sim-cards-on-operators-network-telcos-insist/
[19] Patel K., Han H. & Jain A.K. (2016). Secure Face Unlock: Spoof Detection on Smartphones. IEEE Transactions on Information Forensics and Security, 11(10), pp. 1 – 16. https://doi.org/10.1109/TIFS.2016.2578288
[20] Pocovnicu A. (2009). Biometric Security for Cell Phones. Informatica Economică , 13(1), pp. 57 – 63.
[21] Truecaller. (2021). About Truecaller. https://www.truecaller.com/
[22] Tsay, J. K., & Mjolsnes, S. F. (2012). A vulnerability in the UMTS and LTE authentication and key agreement protocols. In Advances in Information Security. Springer. Vol. 55, pp. 77–90. https://doi.org/10.1007/978-3-642-33704-8_6
[23] Yang, W., Wang, S., Hu, J., Zheng, G., & Valli, C. (2019). Security and accuracy of fingerprint-based biometrics: A review. Symmetry, 11(2), 141–160. https://doi.org/10.3390/sym11020141
[24] Zukarnain, Z. A., Muneer, A., & Aziz, M. K. (2022). Authentication Securing Methods for Mobile Identity: Issues, Solutions and Challenges. MDPI, 14(4). https://doi.org/10.3390/sym14040821.
Downloads
Published
Issue
Section
License
Copyright (c) 2024 International Journal of Applied Methods in Electronics and Computers

This work is licensed under a Creative Commons Attribution-ShareAlike 4.0 International License.




